Recovery Result and Report
How can I check the data recovery result? What is in report?
The scrupulous request about required for recovery files is always highly appreciated by data recovery specialist. However, many computer users do not know the real physical location of their important files, and it is OK if you are one of them. One of the purposes of providing the customer the data recovery report is to sort out the issues like that.
Depending on the operating system type, almost any software application selects some certain default place on the drive in the order to save user’s data - like documents, pictures, or emails. If you skip the question in the online form about important files to recover first, then as the proper measure - the user’s profiles will be considered as the priority to recover.
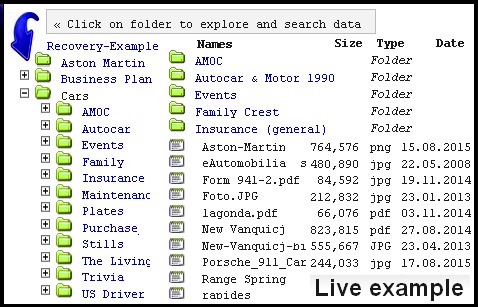
The detailed list of requested or may-be-required files grouped by originally created folder names and chain of directories as the path-finders will give you the good observation of what was retrieved from the defective drive. Along with the user’s files there are many known folders with program files, drivers, operating system itself, and another data that you probably do not care for at all. Obviously, the folders like System Volume Information, WINDOWS, or hidden system files like PAGEFILE.SYS and HIBERFIL.SYS, are not usually included in the recovery report, unless you order to do so. To reduce the size of report and safe your time on reading thousands of file records, we do not include computer data that is not related to user data of interest, such as system or program files.
In general, data recovery report is a set of few files, some of them are lists of all, or individual data folders, another are groups of actual user’s files with the examples of personal documents or family pictures, easily recognizable by the owner of failed drive. The screenshots from some applications like email system or database structures are also available at the request.
Every record about file in the list includes the information of the file size and date of its last modification/creation.
Our lab is able to detect the corrupted files in the cases if the corruption is caused by the physical damage and contain the unreadable sectors. If such corrupted files are detected, they will be moved to the separate location - the list of the “data with errors” will be created and included in the report, too.
